AWS Nitro API Co-signer Architecture
Learn how to install AWS Nitro Co-signer in the following guide
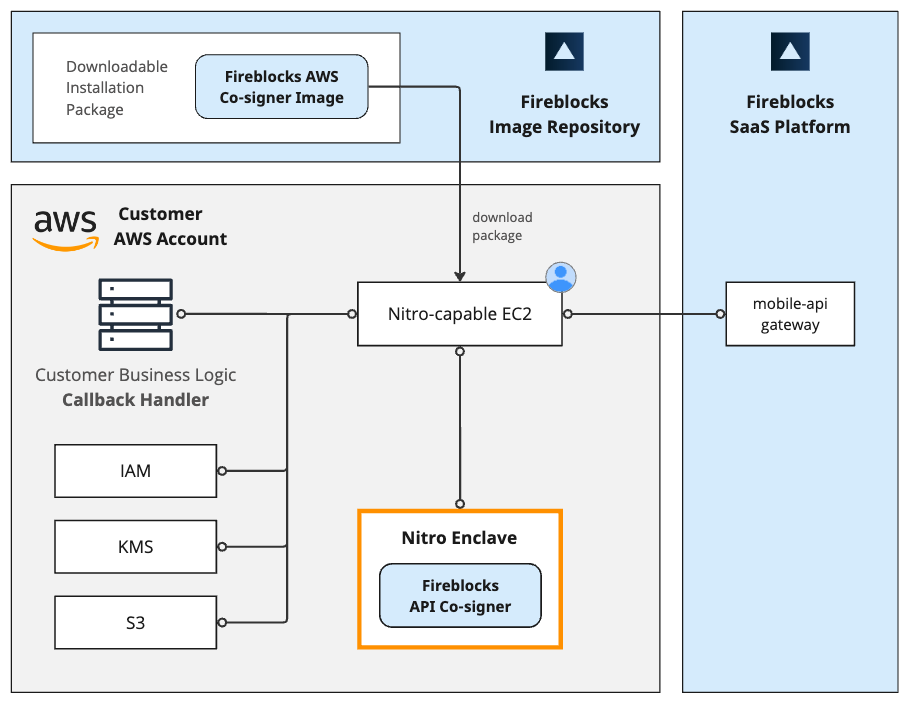
AWS resources used by the Co-signer
The Fireblocks AWS Nitro API Co-signer leverages AWS Nitro Hypervisor technology and attestation mechanisms. It utilizes the following AWS resources:
- EC2 Instance: Nitro-capable VM, through which the enclave operates.
- S3 Bucket: used as the Co-signer's persistent storage and holds the encrypted database of the Co-signer.
- KMS Customer Managed Key: used to securely protect the Co-signer's MPC keyshares, which are stored in the Co-signer's persistent storage within an S3 bucket.
- IAM Role: used to tie everything together by granting only the necessary permissions to the specific resources.
Important: Allocate a separate set of resources for each Co-signer to prevent conflicts and ensure isolation, enhancing security.
This is illustrated in the block diagram below:
Co-signer attestation
Fireblocks uses Nitro’s Platform Configuration Register (PCR) as an attestation mechanism to ensure the enclave image file that is accessing the resources at runtime is signed by Fireblocks.
In AWS, PCR8 (Platform Configuration Register 8) is a part of the Trusted Platform Module (TPM) ecosystem and is specific to environments involving Nitro Enclaves or other secure computing contexts.
In the AWS Nitro Co-signer, PCR8 measures specific details about the Co-signer during the secure boot process. It ensures setup integrity by validating Fireblocks' enclave image signature when accessing the Customer Managed Key (CMK).
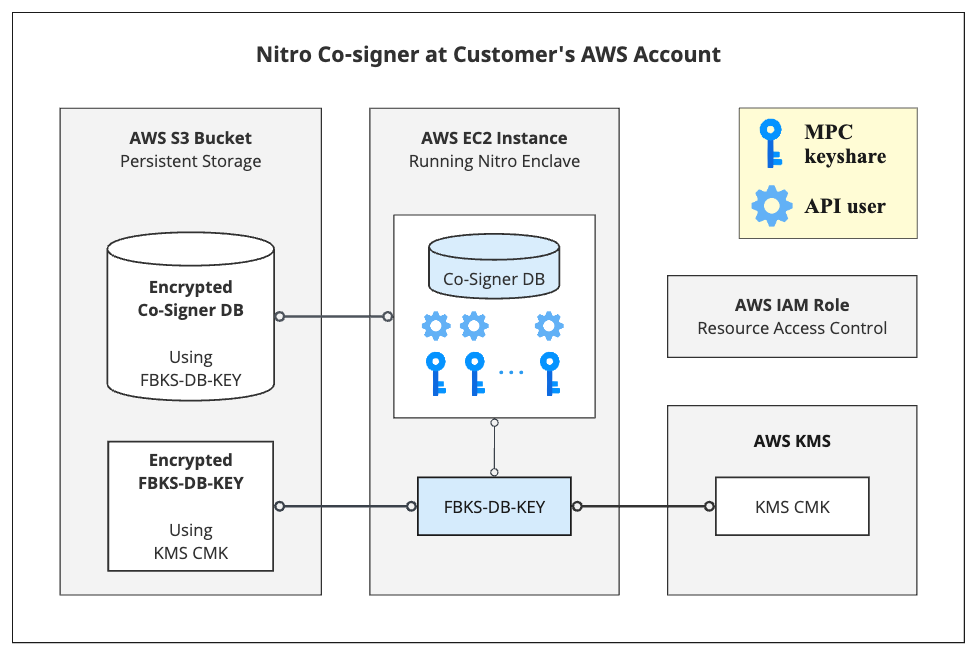
Secure Co-signer database encryption scheme
The following process is implemented to build and secure the Co-signer's database:
- The user creates and configures a symmetric Customer Managed Key (CMK) in the KMS.
- The Co-signer, upon initialization, asks KMS to generate an additional AES 128-bit CBC key:
FBKS-DB-Key - The Co-signer initializes its encrypted database using the key
FBKS-DB-KEY - The Co-signer encrypts
FBKS-DB-KEYusing the CMK. - The Co-signer saves its encrypted database and the encrypted form of
FBKS-DB-KEYin the S3 bucket, serving as its persistent storage - The access to KMS, including the CMK, is restricted using a Fireblocks enclave image attestation signature and the IAM role and policies that were created by the user.
This is illustrated in the block diagram below:
AWS Nitro installation package
The installation package contains an Enclave Image File (EIF) and a set of installation scripts. The EIF is built based on the image containing the common API Co-signer code and the AWS Nitro enclave functionality. This image is scanned for known vulnerabilities, and only then does the build process continue based on the AWS build procedure.
Updated 5 months ago